Archive
Adobe fixes Reader and Acrobat
Not only Microsoft released a bunch of patches to close security holes in their products, but also Adobe now ships updated software to fix several vulnerabilities in Adobe Reader and Acrobat which already get attacked with specially prepared PDF documents to take over control of vulnerable computers.
Users of Adobe Reader and Acrobat with earlier versions than the new 9.2 are advised to install the updated software immediately to protect themselves from the attacks; Adobe rates the vulnerabilities as critical. New versions of Reader are available for Windows, Mac and Unix. Further links for updates for different Acrobat versions are listed in Adobes security advisory.
W32/Induc.A Removal Tool by Avira
Last week a virus that infects Delphi development environments and then the compiled Delphi programs was detected and got some media attention – infected programs were distributed on cover-mount CDs and DVDs on computer magazines and via Download Portals.
Avira developers created a special version of their Avira Removal Tool which is capable of detecting and deleting infected programs. You can download the English version here and the German version here!
Chrome security in limelight with Google OS plan
The techniques Google uses to protect Chrome users from browser-based attacks have taken on new importance with the company’s plan to make the software the centerpiece of a Netbook operating system.
Two weeks ago, Google announced plans for the open-source Chrome OS designed for people who spend most of their time on the Web. The Google Chrome operating system is a “natural extension” of the Chrome browser, Sundar Pichai, vice president of product management, and Linus Upson, engineering director, said in a blog post, with the browser running atop a Linux foundation.
Like the Chrome browser, the Chrome operating system will be built from the ground up with development focused on three key areas: speed, stability, and security. “We are going back to the basics and completely redesigning the underlying security architecture of the OS so that users don’t have to deal with viruses, malware, and security updates,” the post said.
Google representatives declined to elaborate on plans for the operating system, but it’s highly likely it will align closely with what they have done with the browser, particularly given the fact that attacks on the browser now outnumber those targeting the underlying operating system. The number of new browser vulnerabilities has increased rapidly every year since 2003, and the number discovered in Web browser plug-ins has more than quadrupled, according to the National Vulnerability Database.
It’s also notable that Google put features in its browser that are typically associated with operating systems.
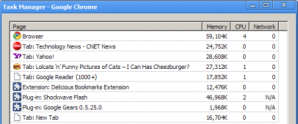
“Google Chrome from day 1 had its own task manager, just like Windows did, showing memory consumption and CPU utilization. I said that’s what an operating system has. It’s a fairly clean translation,” said Billy Hoffman, manager of Web Security Research Group at HP Software and Solutions.
Chrome OS, whose source code is due to be released publicly later this year as Google tries to enlist open-source programming allies, is likely to change the operating system landscape just like Chrome the browser did, prompting rivals to try to match or beat its features.
“The innovation (coming out) of the browser wars is bringing more and better security,” Hoffman said. “The Chrome browser itself is fairly hardened, and we hope they move into more user protections like IE 8 and Firefox.”
Chrome has several design features that optimize security: sandboxing, which restricts privileges of key parts of the browser so it’s harder to coopt them for mounting an attack, and multiprocess architecture, which stores Web sites and Web applications in separate areas of browser memory areas and isolates them from the rest of the computer.
Overall, security experts say Chrome shows that Google takes security seriously and its developers are willing to try new approaches to achieve it.
“Google has done a lot of innovation in terms of security in Chrome,” said Matt Wood, a senior researcher in Hoffman’s department at Hewlett-Packard.
Starting from scratch
Being new to the browser game helped.
“By starting fresh, we had the option to do very innovative things we wouldn’t have been able to do otherwise,” said Ian Fette, the Chrome product manager specializing in security features.
What set Chrome apart when it launched in beta last September was that it splits the browser up into multiple parts. The browser kernel interacts with the operating system and handles only trusted code, storing things like bookmarks and cookies on the computer. Other main components, the rendering and JavaScript engines that figure out how to display Web pages and execute Web-based JavaScript programs, run with restricted privileges in a sandbox that limits access to the underlying system.
Chrome’s initial line of defense is to check a site being visited against several anti-malware and anti-phishing blacklists that comprise Google’s Safe Browsing service.
If some malware evades the safe browsing screen it’s likely to be blocked by Chrome’s sandboxing technology. The sandbox runs an application in a restricted environment, isolating HTML rendering and JavaScript execution to prevent them from writing to the hard drive or registry or accessing files.
“The goal is to make it impossible for malware to install itself and access your data on your local computer,” Fette said.
Chrome also restricts each the browser tab to its own computing process. That further prevents malware from being downloaded or interacting with other Web pages that are open in other tabs.
Automatic updates
Another aspect of Chrome that security experts praise is the so-called “silent” auto update feature. New versions of the browser are automatically updated on computers in the background without the user taking any action.
Chrome checks for updates every five hours using the open-sourced Google Update software code-named Omaha that polls for updates even when the browser is not running. When a new update is available on the Google server, the client automatically downloads and installs it in the background without prompting the user. The new version of the software gets applied when the browser is restarted.
Given that more than 45 percent of Internet users don’t use the latest Web browser version, according to Google research, it would seem that there is a huge need for this.
“Our philosophy is users shouldn’t have to care,” Fette said. “Everything should keep working for them.”
When Chrome first launched in September it had two vulnerabilities that were exploitable. Google released patches for them within 24 hours, he said.
“End users don’t know whether to refuse or accept software updates. Chrome just forces them on people,” Hoffman said. “It’s a good example of not letting users make poor security choices.”
Nevertheless, some want the choice. For IT administrators who want to control software updates themselves, Google recently added options to let enterprises customize when and how they get Chrome updates, Fette said.
Chrome, which released its latest security patch this week, had 14 exploits last year based on statistics on the Milmw0rm site, Wood said. However, any comparisons to the number of exploits or patches on Chrome compared to Internet Explorer or Firefox are difficult because Chrome has far fewer users and thus is less targeted by attackers, he said.
Tricking the user
Chrome does a great job of protecting against exploits of vulnerabilities in which attackers sneak code through a hole in the browser to install malware or run code on the computer, experts said. However, it’s not so good when it comes to protecting them against Web-based attacks like cross-site scripting, cross-site forgery, SQL injections, and phishing, in which an attacker tricks users into doing something they didn’t intend via the browser, they said.
“One thing Google needs to work on where they haven’t really focused is on stuff like user security,” said Wood.
Chrome lacks the plug-in support Firefox has to protect against malicious scripts hiding on Web sites. For instance, there is no Chrome equivalent to the NoScript Firefox plug-in that lets users choose which scripts on a site they want to run or block. But that is likely to change.
“We are in the middle of building out our own browser extension system so that something like NoScript could be done,” Fette said. “For many people it’s a noisy option. It asks a lot of questions and if you’re not focused on security it could be hard to make it work.”
Internet Explorer 8 offers a cross-site scripting defense mechanism that protects users against those type of attacks, Wood said.
Google is evaluating cross-site scripting protections, but, Fette said, “You have to make sure it’s based on standards and won’t break sites.”
IE also lets users turn off JavaScript. Chrome doesn’t, but it does sandbox JavaScript.
“If you turn off JavaScript you may turn off navigation on a bank site” or otherwise render a site unusable, Fette said. “It’s not an option we feel is viable, so we don’t offer it.”
Two other popular exploit targets, Adobe Flash and Adobe Reader, are not sandboxed in Chrome because doing so caused problems with auto update or other features, he said. “Sandbox is not a panacea,” Fette said.
The two-browser prescription
Jeremiah Grossman, chief technology officer and co-founder of Whitehat Security, suggests that people use two different browsers for the safest experience: Chrome for “promiscuous Web surfing” and Firefox with the NoScript plug-in for important activities such as checking e-mail or online banking.
Asked to comment on that suggestion, Fette said that because each Chrome tab is a separate process the system has the same protection as using two different browsers.
Finally, Chrome should do a better job at password management, according to Wood. None of the other browsers does better, but Google should raise the bar, he said.
“There is no real security with password management. You can open it up and see all the passwords in clear text,” he said. “A browser needs a good password manager. People can’t remember all the passwords for all the sites on the Internet.”
In response, Fette said someone with access to the computer already can do plenty of damage–for example installing a key logger to monitor what the user types.
“Chrome came out and lit a fire under Firefox and IE. It’s driven a lot of innovation and a lot of that has been in security and general usability,” said Wood. “We’re moving toward a more secure browser. A lot of that has to do with getting people to understand about the threats that exist on the Web.”
avast! 5 is coming… soon!
After a long span of timei am glad to know about upcoming avast! version 5. The first thing to note is that the product is coming relatively soon. Namely, avast team currently planning to release it this October.
The product will be offered in three flavors: a free AV (that will supersede avast! 4.8 Home Edition), a paid AV (successor of avast! Professional Edition) and a full Internet Security suite. As usual, all customers (or users) with a valid avast! subscription will get a free upgrade to this new version.
The free AV will, of course, contain all the features from the existing Home Edition, plus a couple of new extras (I’ll be sharing more details on the blog as time goes by). The paid AV now includes a new virtualization module as well as all the features from the free AV and features previously exclusive to avast! 4.8 Pro. And finally, the suite adds an antispam and firewall module and will thus provide you with a complete, worry-free protection.
All three products will share the same antivirus engine (e.g. all of them will still have exactly same detection rates) that has been substantially improved and optimized. It may sound like a cliché, but it’s a fact: the new engine can detect more viruses, while actually consuming less resources.
The performance optimizations were not confined to the AV engine only; the program now uses various tricks to feel as light as possible and to not interfere with your work in any way. For example, we have radically improved the time it takes the computer to boot, making the slowdown imposed by avast! almost unnoticeable. I’ll be very interested in getting some feedback from you on this one (as soon as you get a chance to test it – please read on).
Starting with version 5, avast! now officially supports heuristics (proactive detection), although between me and you, many of the stuff has already been present in the previous versions – but we haven’t marketed it in any way. Also, detection of Potentially Unwanted Programs (PUPs) has been added. Additionally, version 5 includes a new code emulator (or in fact, a dynamic translation module, to be technically correct) that will be of great help e.g. when unpacking malware samples packed/protected by unknown packers (as is the case pretty often).
All three products also feature a new user interface which has been completely redesigned for this new version. We’re abandoning the dual (simple vs. enhanced) UI model and replacing it with a single comfortable console, designed for both novice and experienced users. I’m attaching a screenshots to give you an idea of what the product actually looks like.
An early look on Microsoft Security Essentials
The beta version of Microsoft Security Essentials, a free program that fights viruses and spyware, is now available for download (only in certain countries and limited number of downloads). The app, previously code-named Morro, replaces Windows Live OneCare and fights the usual rogues’ gallery of PC threats, including worms, Trojans, and other troublemakers.
Security Essentials runs on Windows XP, Vista, or Windows 7 (beta or release candidate), and does pretty much what any good anti-malware app should do. It automatically downloads virus and spyware definitions; offers real-time protection that scans downloads and attachments, and looks for suspicious file and program activity; and runs unattended scans at a time that works best for you (e.g., Sunday morning at 7 a.m.).
The program’s interface is clean, A green icon shows you’re protected. And a red-orange icon means trouble, such as if real-time protection is turned off.
While this sort of visual reporting is common among anti-malware apps, Microsoft’s presentation is jargon-free and easy to follow.
Security Essentials’ Settings tab provides fast access to advanced tools that power users might reconfigure. Example: The ability to scan removable devices such as USB flash drives, a feature that’s turned off by default. You can schedule scan times too. This is just a news about what is happening on in the catagory of security software to all “Computer Inspiration” readers and I personally don’t recommend to switch to this application which is still under beta testing.



Recent Comments